This post is the second part of a three-part series on proxy blocks, covering peer-to-peer proxies and responses. (first part, third part)
Open proxies – shared IP addresses accessible anywhere through free or paid services – have been blocked on Wikimedia projects for over 16 years, due to their usage in bypassing IP-based anti-abuse mechanisms.
Throughout that time, however, the landscape of open proxies and the types of proxies available have changed. Where traditional VPNs are easily identifiable as such, the rise in peer-to-peer proxy networks have allowed bad faith actors to avoid identification more easily by posing as residential users, which in turn significantly increases the collateral costs of blocks.
Peer-to-peer proxies
Peer-to-peer proxies expand the scope of proxy blocks significantly. Where VPN IPs are generally exclusively used by people who intentionally connected to that proxy service, peer-to-peer connections can turn any IP into a proxy.
Various services exist to facilitate peer-to-peer proxies, creating a network where internet traffic of one user is funneled through the internet connection of another. Bad actors can use these peer-to-peer proxy networks to access residential IP addresses in any part of the world.
Unfortunately, the nature of peer-to-peer proxies means that collateral effects, i.e. users affected by proxy blocks who are not using proxies, are significantly more prevalent. This is because blocks on these IPs or ranges affect everyone connecting on those IPs, not just the computer being used as a proxy. There are also instances where peer-to-peer proxies may be running on a device without the knowledge of the device’s user.
This issue of collateral effects is particularly problematic with carrier-grade NAT (CGNAT) configurations, where many users connect through a singular IP address. If any one of those users is using a peer-to-peer proxy, and the IP is blocked, no one using that IP can edit.
Increases in blocks
Before 2020, blocks were generally placed on proxy IP ranges individually, when found by administrators and CheckUsers. As peer-to-peer proxies became more available, the English Wikipedia saw significant abuse from these proxies, leading to the automation of their identification and blocking.
ST47ProxyBot, run by an English Wikipedia administrator/checkuser and active only on that project, was approved in April 2020, and started running shortly after. Its mandate is to automatically identify and block open proxies, which did not significantly disrupt the trend. In August 2021, its scope expanded to include peer-to-peer proxies, spiking the English Wikipedia’s monthly proxy blocks from 78,000 in July 2021, to over 440,000 in August. This change was described in more depth on the administrators’ noticeboard.
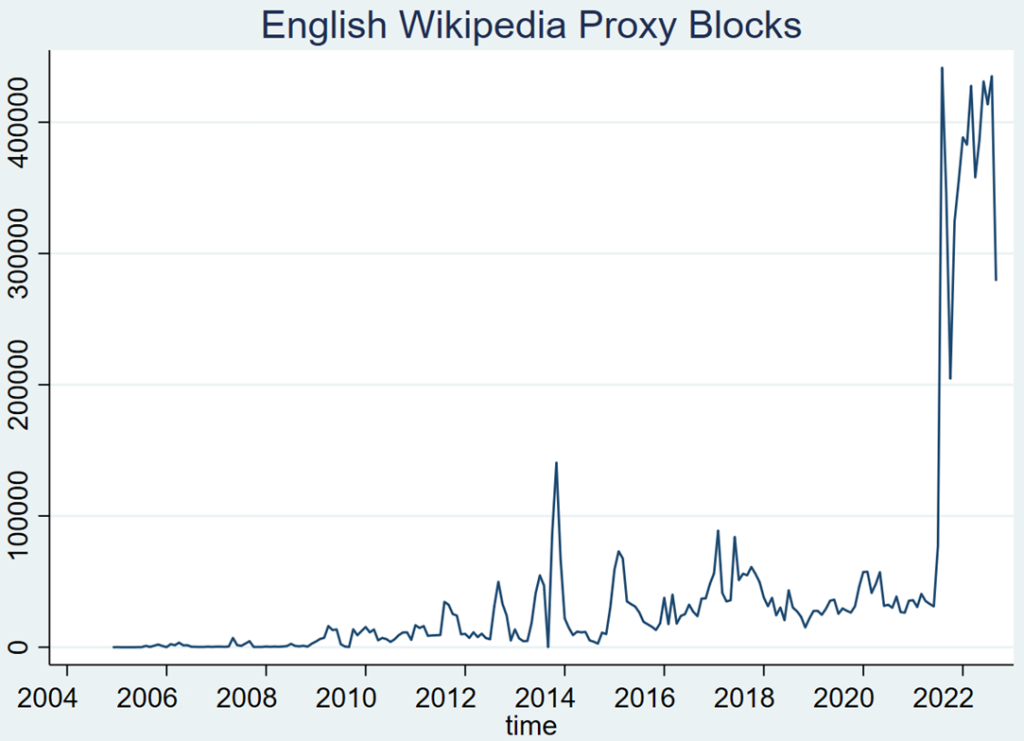
Given the highly dynamic nature of peer-to-peer proxies, it starts with a short duration and extends the block as needed; many of the above numbers are re-blocks of the same individual IP addresses. They are also often hard-blocks, meaning that they apply both to logged-out and logged-in users.
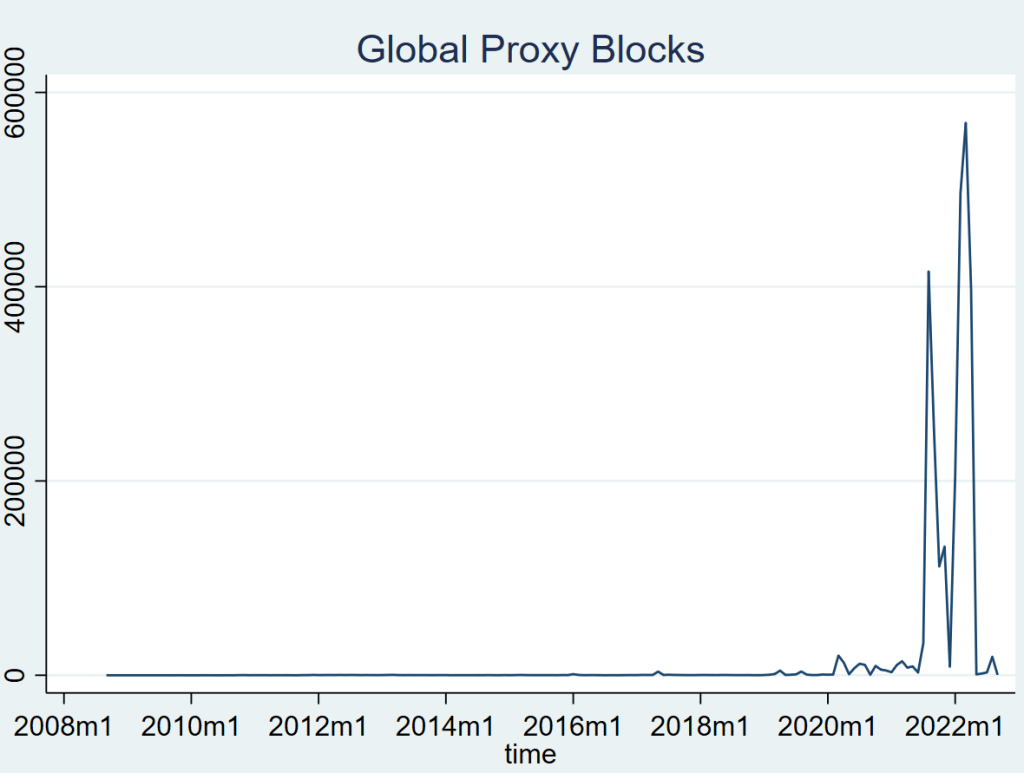
Around the same time, Stewards set up a script to mirror many of ST47ProxyBot’s English Wikipedia proxy blocks as global blocks, which apply on all Wikimedia projects. This resulted in spikes of similar magnitude, increasing from 33,000 blocks in July 2021 to 415,000 in August.
Despite the English Wikipedia’s proxy-blocking bot having made over 5.7 million blocks since its inception in March 2020, only roughly 165,000 are currently active. (which is 97% of all active English Wikipedia proxy blocks, many/most of which are normal VPNs)
And despite over 2.8 million global proxy blocks being made in the last 2 years, at the time of writing there are only roughly 29,000 currently active. Stewards ceased mirroring of ST47ProxyBot’s blocks in April 2022, after concerns about the collateral effects were raised on Meta-Wiki.
Many of these peer-to-peer proxy blocks are of CGNAT IPs, where singular IP addresses may be used by hundreds of users. Just one person using that IP as a peer-to-peer proxy can result in that IP being blocked. And as these blocks are often hard-blocks, it prevents both unregistered users and users with accounts from editing. The next post in this series discusses the collateral effects from these blocks, and its implications for equity and growth.

Can you help us translate this article?
In order for this article to reach as many people as possible we would like your help. Can you translate this article to get the message out?
Start translation